People have long been predicting the death of the password, but here we are – more than halfway through 2017 – and passwords are still as commonplace (and bad) as ever. The traditional password remains the primary authenticator for users across virtually every system, website, and application. At the same time, the traditional password also serves as the user’s worst enemy, with password fatigue and creation rules pushing users toward lazy, less secure passwords, and padding the hacker community’s database of cracked credentials. And while they’re here to stay for the foreseeable future, the way we use them and complete the authentication process is changing. This post explores the current state of online authentication, where we expect it to go, and best practices for staying secure.
Passwords – We’re Really Bad at Them
The eternal struggle with passwords is between security and convenience. The better the password, the more difficult it is for hackers to crack. But it’s also more difficult for the user to remember. Most users are more concerned with day-to-day convenience, so they take shortcuts by making simple passwords or reusing the same password on multiple accounts. It’s estimated that 65% of people use the same password across all their accounts. This is one of the weakest security practices, and it’s rampant among users today – especially millennials.
A recent study found that millennials are far more likely to use extremely weak passwords. This is especially troubling because it’s the millennial demographic that is the most connected and leaves the largest Internet footprint. As millennials enter the workforce, they bring their weak passwords with them, increasing the risk to their employers.
Clearly, there are a lot of weak passwords out there, and that number is only increasing. According to a recent report, 3 billion user accounts and passwords were stolen in 2016, with 8.2 million breached every day. It’s estimated that 300 billion passwords will be at risk of theft by 2020. A good chunk of these weak and easily hackable passwords can be attributed to the explosion of the Internet of Things (IoT), where Internet-connected devices come equipped with passwords like “1234”. These insecure devices, combined with the ever-increasing number of online identities and accounts required for daily life, contribute to this vulnerable mass of lackluster authentication that puts both users and businesses at risk.
| Credentials Stolen in 2016 vs. Credentials at Risk in 2020 |
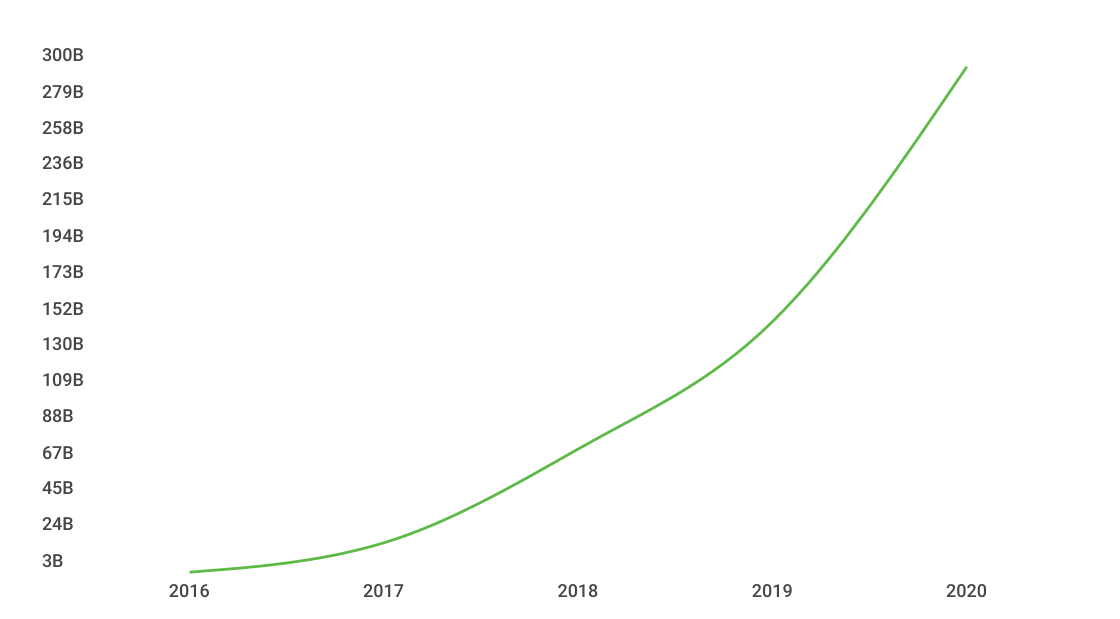 |
We’re all looking for ways to get more out of our passwords, so we don’t have to memorize 50 different random strings of letters and numbers to keep ourselves safe. So, what are our options?
Password Consolidation
One of the easiest ways for users to maintain complex and varied passwords is through a password management application. A password manager generates random strings for each of your accounts, and auto-populates them into forms so that you don’t have to memorize them. Of course, you have to memorize a long and complicated master password to access your account – but it’s still far more convenient for most users. While there is some debate over the risks of putting all your eggs in one basket (and these services are extremely high-value targets for hackers), there is no doubt that password managers are a significant security upgrade compared to reusing the same simple passwords for all of your accounts.
Another way users are alleviating password and account fatigue is through the use of social logins – mostly through Facebook or Google. And, while tying your Facebook account to unrelated accounts in order to ease the login process isn’t necessarily insecure (so long as your Facebook password is strong), it does pose some concerns about privacy. Users should be aware that granting these third-parties access to social media accounts also grants them access to the information that lives there. Before using a social login, make sure you fully understand what personal information you’re potentially exposing as a result.
From an enterprise perspective, single sign-on (SSO) should be the standard for organizations running an array of applications and tools that require multiple accounts. SSO allows for the integration of applications within your organization’s infrastructure, and allows employees to keep only one secure password. SSO also has the potential to dramatically simplify enterprise enforcement of password policies.
Multi-Factor Authentication
The best available solution we have to strengthen account security is to add another step to the authentication process. Multi-factor authentication (MFA) or two-factor authentication (2FA) is rapidly being adopted by organizations and security-conscious users. The concept is simple: 2FA requires something you know (a password) and something you have (a phone, token, fingerprint, etc.). This creates an extra layer of security, where a hacker would need to have access to both your password and a physical object to infiltrate your account. Some have estimated that 80% of breaches could be prevented by some form of MFA.
|
Multi-factor Authentication |
 |
Multi-factor authentication has been around since at least the early 2000s – but is only now rising into the public consciousness. Large companies like Google and Amazon are now not only offering multi-factor authentication, but encouraging its adoption. Microsoft is allowing users to ditch passwords completely by using an authenticator app to approve sign-ins. From an enterprise-level, companies like Duo Security allow organizations to implement MFA for all employees in conjunction with SSO.
While using MFA is a more secure practice than authenticating with only a password, it is not without its weaknesses. SMS messages, the most common second form of authentication, are susceptible to determined hackers, who can intercept or reroute cell phone communications. Even physical tokens have been breached in the past, undercutting the entire MFA process.
MFA isn’t perfect, but it is without a doubt the easiest and most effective way for users to elevate their security, and we encourage its adoption, both for personal and enterprise use.
Biometric Authentication
Some services are now giving users the option to authenticate themselves through a unique physical characteristic rather than a secondary device. Yep, that means fingerprints, retinal scans, facial recognition, and the like. It may seem like science fiction, but this MFA variation is being used with increasing regularity, especially as the technology moves into mass-consumer electronics. The latest mobile phones for both iOS and Android systems, for example, now have built-in fingerprint scanning and facial recognition.
Large companies, especially banking and financial institutions, have taken to biometric authentication to increase security and provide a smoother user experience for customers.
- MasterCard has introduced the ability to approve a transaction by allowing users to verify their identity by taking a selfie, using facial recognition technology to authenticate.
- Barclays is now giving customers the option to use voice recognition over the phone rather than answering security questions.
- Wells Fargo gives executive users the ability to login to their mobile banking account with retinal scanning technology.
While these methods are promising, biometric authentication is still relatively new and has vulnerabilities of its own. Biometrics can still be hacked, or faked, and they can’t be changed or reset the way a password can. In other words, you can’t get a new fingerprint if yours gets compromised. A credential like this poses a different kind of risk, as biometric data has specialized uses, most notably in the criminal justice and legal system, that would make its exposure disastrous for a breached user.
Contextual Authentication
All of the options considered so far have relied on a second piece of data to authenticate. But what if there was a form of MFA that took into account many factors to authenticate based on the context of the request? Google has recently implemented a similar program, calling it a “tiered access approach.”
It works like this: The system makes a decision to grant access based on user and device criteria, like whether or not the device is running the latest operating system and security patches, the network used to request access, the behavior of the device, and – yes – whether a valid password has been provided. Google has defined trust tiers that must be met if a user is to be granted access to a particular application or set of data. Users and devices are assigned risk profiles that are assessed after the normal authentication process in order to determine if access should be granted. In this system, passwords move from their position as the primary authenticator to a single factor among many.
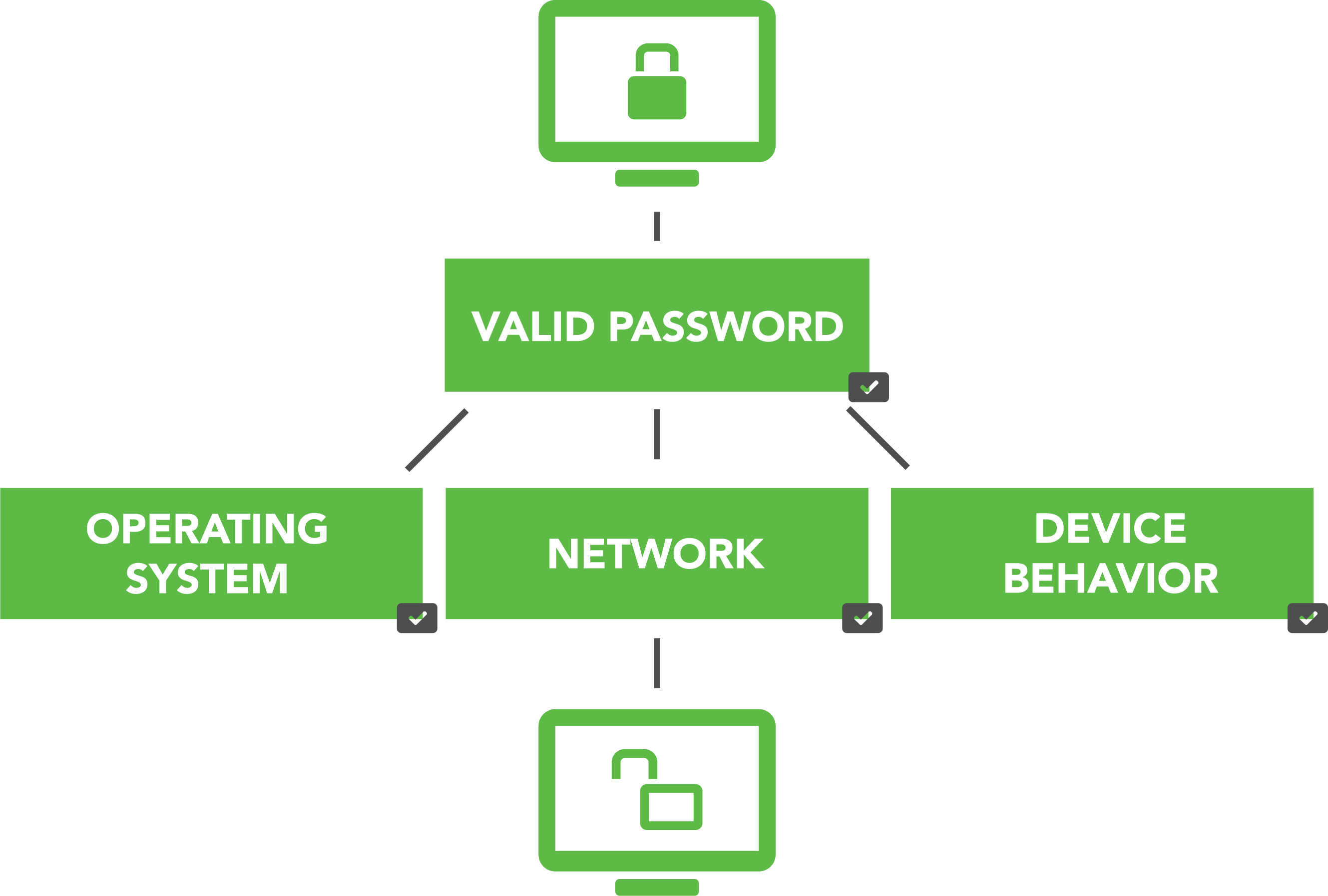 |
| Contextual Authentication Diagram |
Think of it as MFA on steroids, with the user providing one factor and contextual elements providing the rest. With contextual authentication, security happens behind the scenes, and the user experience is unchanged. And while Google’s transition has made waves, this method of authentication is still fresh, and the technology and effort required to implement a widespread system like this is not economical for most companies yet.
Making Sense of It All
There are plenty of options for password security on the table – and new ones appear all the time. But for most companies, simple and commonsense best practices are still the way to go.
First, users and organizations alike should embrace multi-factor authentication. This is the strongest and easiest way to protect yourself and your enterprise from password cracking and rogue logins, and increase security exponentially with minimal effort. Whether it’s via SMS text, push notification, or physical token, an account utilizing MFA is almost always more secure than an account that isn’t.
From an enterprise perspective, organizations should take the opportunity to invest in access management and security technology. We believe that both MFA and SSO should be standard for corporate accounts, and implemented at all organizations of appropriate size and user base. Additionally, companies need to make a focused effort to train their employees in basic cyber security and password management principles. We recommend a strong but user-friendly password policy, as well as regular e-mail awareness training and social engineering (phishing) campaigns.
Want more strategic insights like this?
Subscribe to Focal Point's Risk Rundown below - a once-a-month newsletter with templates, webinars, interesting white papers, and news you may have missed. Thousands of your colleagues and competitors have signed up! You can unsubscribe at any time.










