We, the users of the Internet, have been the targets of phishing scams for over 20 years. Early instances include AOHell (circa 1995 – when the term “phishing” first took off) and the LoveBug (early 2000), which spammed victims’ address books. While these early phishing attacks were decidedly simplistic, today’s phishing attacks are far more advanced and difficult to stop. With a higher volume of high-value data stored online, our money, identities, and critical corporate data are all at risk. The stakes are much higher now than in the mid-90s.
Despite having two decades to figure out how to foil phishing scams, a remarkably high percentage are still successful. And email phishing is still the dominant attack form, with 44% of 2016 incidents social in nature (these email phishing scams are also the top delivery vehicle for malware and ransomware). So why are they still so successful? One reason is because phishing attacks prey on our human nature. Attackers are betting that we’ll click before we report, that we’ll trust rather than verify, and that we’ll respond to any email that has our corporate logo at the top. At the heart of that problem is a serious lack of training. We’ve also seen a rise in highly sophisticated, slow-burn attacks. Malicious attackers are spending more time creating personalized campaigns that target high value data and employees, sometimes investing many months into the research and planning of the attacks.
As a company that offers social engineering services and customized cyber awareness trainings, we’ve spent years tracking phishing trends and developing strategies to stop them. Recently, though, we’ve seen several novel phishing schemes (including one by our own social engineering team) that highlight the way these attacks are changing.
Disclaimer: For the privacy and safety of the companies we research and work with, we have redacted or changed company names, locations, and industries in the following accounts.
Lesson 1: Phishing Attacks Rely on Our Click-First Mentality
After falling victim to a recent spear phishing attack, a company requested that we assess the control breakdowns and help prevent similar attacks in the future. It quickly became clear to our team that this attack was successful because employees were too click-happy. Rather than taking the time to scrutinize emails and report suspicious behaviors, employees clicked… and clicked… and clicked… and caused some serious damage.
In these employees’ defense, this was no simple phishing attack – but that’s the point. Today’s phishing attacks aren’t simple. Hackers are spending days, weeks, even months researching companies and crafting personalized emails that resonate with their targets. Let’s take a look at the three phases of this attack.
Phase 1: Planning
The goal of this attack was to gain access to employees’ payroll information, change their bank account numbers to offshore accounts, and intercept their paychecks. Through some light research, the hackers figured out the dates for spring break for most schools in the target area, as well as the dates when the company was likely to process payroll. The attackers set this as the window for their attack. With many employees out of the office, the attack would be more difficult to detect and more difficult to stop.
With their timeframe in place, the attackers needed to gain access to at least one employee’s email to start their campaign. To do this, they set up a fake email account that emulated the email address of the CEO and sent a simple phishing email to a handful of employees. Most didn’t take the bait, but one did – and that’s all they needed.
The email asked her to review a Word document. But in order to read it, she had to provide authentication credentials – a somewhat unusual but not unheard of request. Once the attackers had her credentials, they lurked in her inbox, gathering information about the company.
 |
| Screenshot of the fake login page used to gather employee credentials |
As you can see in the above screenshot, the hackers weren’t sloppy with their initial email campaign. The attachment looked official, complete with impeccable grammar, and the fake login page was sold with official Microsoft logos.
Phase 2: Execution
After some time passed, the hackers used the breached employee’s account to launch an email campaign on behalf of the CEO, asking employees to update their Workday credentials (the company’s payroll system) before the next pay period began.
Knowing that a massive email campaign would spark suspicion, they sent the emails in small waves. They also created a special folder in her inbox that intercepted replies, which the attackers monitored to erase responses and keep the account owner unaware.
The hackers also took special care in crafting the perfect email. In the first wave, they sent emails that had flawless grammar, used familiar syntax, and mimicked a corporate tone.
Phase 3: Success
Once the emails were sent, employees started clicking.
By the end of the fourth wave, 50+ employees had clicked the link and submitted their Workday credentials. With access to their Workday accounts, the attackers changed employee banking information to offshore accounts, and routed the payroll checks through those accounts and onto other places.
Beyond the phishing emails, what broke down? Well, the manual control within the payroll department – one that requires a payroll employee to manually “Approve” each account change – was not sufficient. Despite receiving 50+ account change requests in one pay period (for a company that averages 10 in that span), the payroll employee did not sound the alarm.
In total, the hackers stole around $120,000.
Lesson Learned
After meeting with the company, we learned that they had not performed social engineering prior to this attack, and their cyber awareness training had room for improvement. This lack of training and testing left employees unaware of how to recognize sophisticated malicious behavior or report suspicious emails.
Improved cyber awareness training with clear processes on how to report unusual emails or behaviors as well as regular testing to heighten employees’ vigilance can change the “click-first” mentality. In addition, implementing a tool that identifies emails from an external source can help employees take the time to stop and evaluate whether it’s from a trusted source.
Lesson 2: Phishing Attacks are Successful Because We Prefer to Trust Rather Than Verify
A company recently requested that we help them trace a phishing attack that resulted in the theft of more than $200,000. After diving in, we concluded that this organization – which relies heavily on third parties – was attacked through a breach at one of its vendors.
Disguised as a third party, the hackers sent the company’s finance team an invoice for $212,000 with a new ACH number. Production was under way and an invoice for this amount was expected. The hackers explained away the new ACH number by citing routine changes in the accounting department of the company.
Rather than verifying this change with an approved contact, the company paid the invoice with the new ACH number.
However, a few weeks later, the real vendor reached out and asked for their payment. They wanted the $212,000 payment before they finished production. When the company went back to check their records, they discovered that the email they received a few weeks prior was actually from comp@connpanyname.com rather than comp@companyname.com (notice the subtle change in the domain), and that their payment went to a bank account in Kuala Lampur while the vendor was based in mainland China.
Lesson Learned
In this case, it’s pretty clear that the company’s third-party vendor had been breached and the attackers were leveraging the data they gained through this breach for even greater financial gain. While this allowed the attackers to craft a very targeted campaign, a verification process for changes to vendor information could have helped foil this attack. In addition, a robust vendor risk management program could have given the company a better understanding of its vendors’ security and privacy policies and procedures.
Lesson 3: Personalization is Playing a Big Role in the Success of Phishing Attacks
A company recently requested that we test their cyber resiliency to phishing attacks. This time, we got to be the hackers, and using publicly available information from their website and sources like LinkedIn, we were able to craft a very customized campaign, which yielded a high success rate.
After creating a fake LinkedIn account, our team connected with nearly 800 employees at this company and leveraged the info on these pages to build an email list. In accordance with our pre-determined rules of engagement, our team built an email that targeted recipients on a personal level.
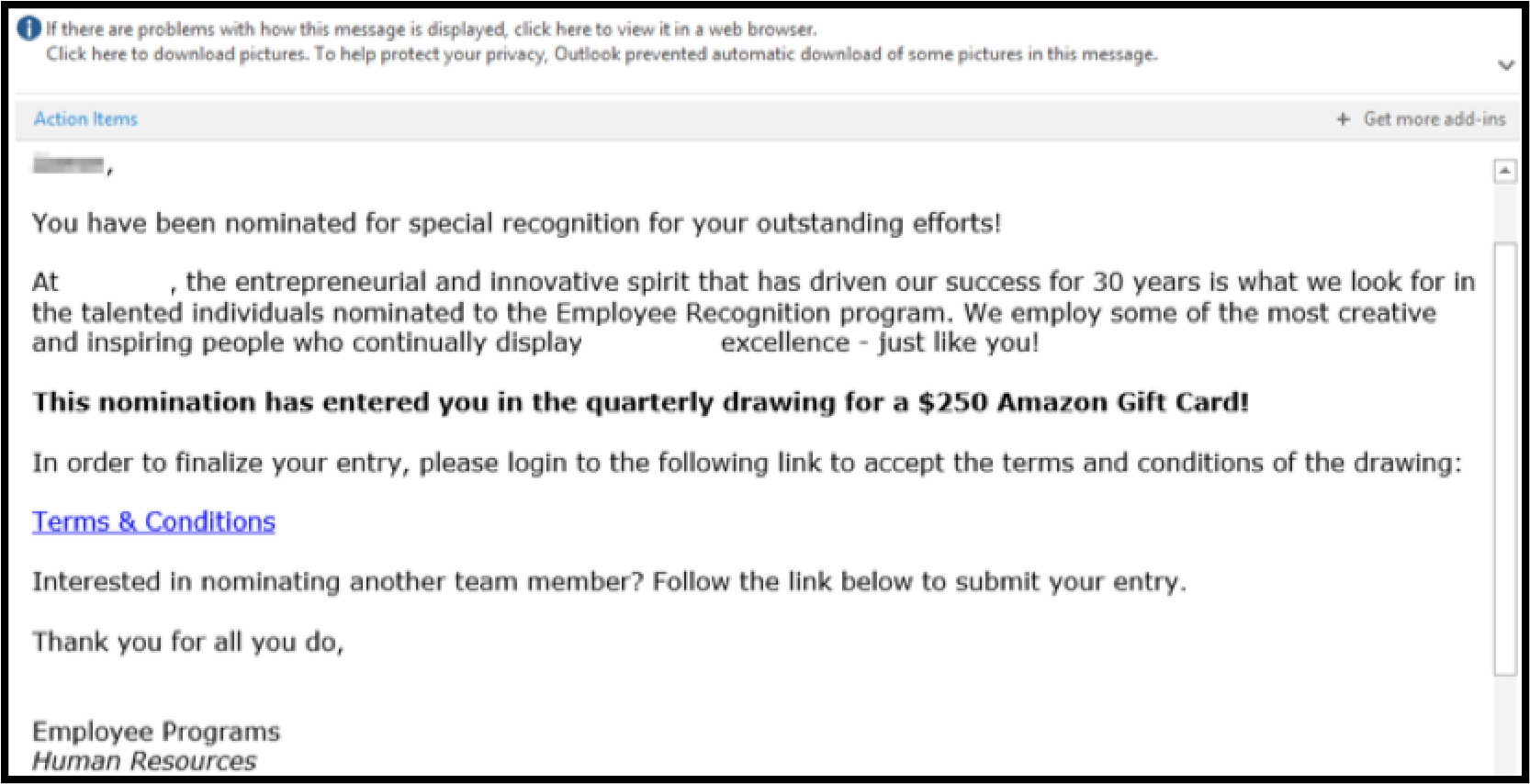 |
| Body of the phishing email used to gather employee credentials in this social engineering campaign |
The email notified select employees that they had been nominated for an employee recognition award. In order to receive their award (an Amazon gift card), the employees were told they needed to agree to the terms and conditions. Upon clicking the link, they were brought to a cloned version of the company SSO page (the URL was just one letter different from the company’s official SSO page) and asked to enter their credentials.
The emails went to 450 employees. Nearly 250 opened the email, and more than 130 logged in. Once they logged in, employees were taken to a landing page that mimicked the corporate website where they downloaded the T&Cs as a Microsoft Word document.
The document prompted employees to enable macros in order to view it in its entirety. Macros are disabled by Word by default, but the document included step-by step-instructions to allow them, which a number of employees followed without question.
Those who enabled the macros kicked off a PowerShell script that sent an outbound connection to an outside server that requested the full payload. While a corporate security tool blocked a number of these connections, 19% of the connections were still successful. This granted our team command-line access to the host as the compromised users, giving us access to a number of valuable internal resources.
On top of all of this, a number of employees who received these emails responded to them and asked for technical assistance. Our team asked 18 of them for their login details in order to assist, and three of them obliged. Had we chosen to, we could have leveraged this position of technical authority for further campaigns.
Lesson Learned
A lot can be learned about a company and its corporate identity from very public sources like social media. Hackers are able to leverage email conventions, titles, and company branding from these sources to build highly customized campaigns that make it extremely difficult for employees to detect suspicious behavior. This example highlights the importance of testing employees so they are aware of the evolving tactics attackers are using, and then building robust training on how to recognize and report these attacks. This training should include best practices for social media, like evaluating connection requests on LinkedIn and regularly reviewing and updating personal privacy settings.
Want more fascinating case studies like this?
Subscribe to Focal Point's Risk Rundown below - a once-a-month newsletter with templates, webinars, interesting white papers, and news you may have missed. Thousands of your colleagues and competitors have signed up! You can unsubscribe at any time.










