You’re a CEO. You’re standing in a room with the CEOs of your two top competitors. You look to your left, and you look to your right. Odds are, two of the three of you will suffer a security breach as a result of a third party.
According to research from the Ponemon Institute, which surveyed more than 1,000 CISOs and other security and risk leaders, roughly 61% (just shy of two-thirds) of U.S. companies have experienced a data breach caused by a third party.
What’s fueling the rise in third-party security and privacy incidents?
Increased Complexity
For most companies, a reliance on third parties (particularly those that help process data) has become mission critical for business success. According to expert studies, more than 70% of organizations have a moderate to high level of dependency on external entities, including third, fourth, or fifth parties. And the number of third parties continues to rise. The Ponemon research found that, on average, companies share their data with 583 third parties. While Fortune 100 organizations with vendor counts in the tens of thousands push that average up, 58% of organizations still say they share information with more than 100 third parties. Regardless of where the number falls, the point remains – it is increasingly difficult to extend your enterprise privacy and security controls to hundreds of other companies, all while keeping up with other day-to-day responsibilities.
Insufficient Resources
Managing third-party risk can be a resource-intensive process. Less than 40% of companies believe they have sufficient resources allocated to their third-party risk management, and even fewer think their current program is highly effective. Despite the staggering number of breaches resulting from ineffective third-party risk management, these programs continue to make due with limited budget, employees, and technology.
Outdated Models
For many companies, the third-party risk management approach has had little change in recent years, despite the increased complexity of their third-party ecosystem. Siloed business functions each assessing their own vendors, ineffective tools, and incomplete or unsophisticated assessment models all compound the problem. New approaches to third-party risk management have emerged in recent years, but adoption remains limited to only the highest-performing organizations.
How Are Top Organizations Handling Third-Party Risk
Despite the obstacles listed above, some companies are excelling at managing third-party risk. They’re the high-flying CEO in the room who now has a leg up on his two competitors, who’ve suffered embarrassing and costly breaches as a result of sloppy risk management practices.
What do the best companies do? Much of it is obvious, though easier said than done. The best vendor risk management programs are comprehensive (evaluating all third parties to some extent), contextual (documenting how each third party interacts with your data), deep (often going beyond third parties to fourth and fifth parties for critical relationships), and backed by leadership (operating with the full support of your board and senior leadership).
But these high-performing third-party risk management programs are also riding a set of trends that are positioned to remake this critical risk management function in 2019 and 2020. These top trends include:
A Push for Continuous Monitoring
Gone are the days when initial onboarding and due diligence constituted effective third-party risk management. Today, an initial or annual assessment is simply one piece of the puzzle. The most mature TPRM programs are moving toward continuous monitoring, in which the shifting nature of third-party relationships is acknowledged and reckoned with. Continuous monitoring, often supported by a technology solution, prioritizes frequent evaluations of how third parties interact with your data and the level of risk exposure they create. Of course, all third parties won’t be treated the same, but taking an adaptive risk management approach for your most important vendors allows leadership to make near real-time decisions about risk management and mitigation strategies. It also gives your organization visibility into the ongoing changes in your third party’s processes, personnel, and technology that may increase or decrease the risk to your organization.
Standardized Frameworks
While we have yet to see a true, unarguable industry framework for third-party assessments emerge, the most mature TPRM programs are moving away from home-grown assessment methodologies and consolidating around a few common assessment templates, such as the SIG questionnaire from the Shared Assessments Group, the CAIQ from the Cloud Security Alliance, or the VSAQ from the Vendor Security Alliance. Some industry groups have also begun pooling resources to standardize third-party assessments, such as the TruSight initiative founded by leading financial services companies, including American Express, Bank of America, JPMorgan Chase, and others. Standardized frameworks allow for more accurate risk comparisons between third parties, and often simplify the burden on your third parties by allowing them to complete a single questionnaire for multiple customers and clients.
Centralized Third-Party Risk Management
Third-party risk management is often fragmented, siloed, or operating with minimal visibility. Mature programs have made a concerted effort to centralize risk management so that an approved pool of third parties exists for the entire organization. In midsized organizations, this effectively eliminates the siloes between business functions, reducing duplicative efforts and sometimes reducing the total number of third parties needed by the organization. In larger organizations, or those with subsidiaries or independent divisions, significant cost savings can be realized by adopting a “clearinghouse” model that assesses and approves third parties for use by the entire organization.
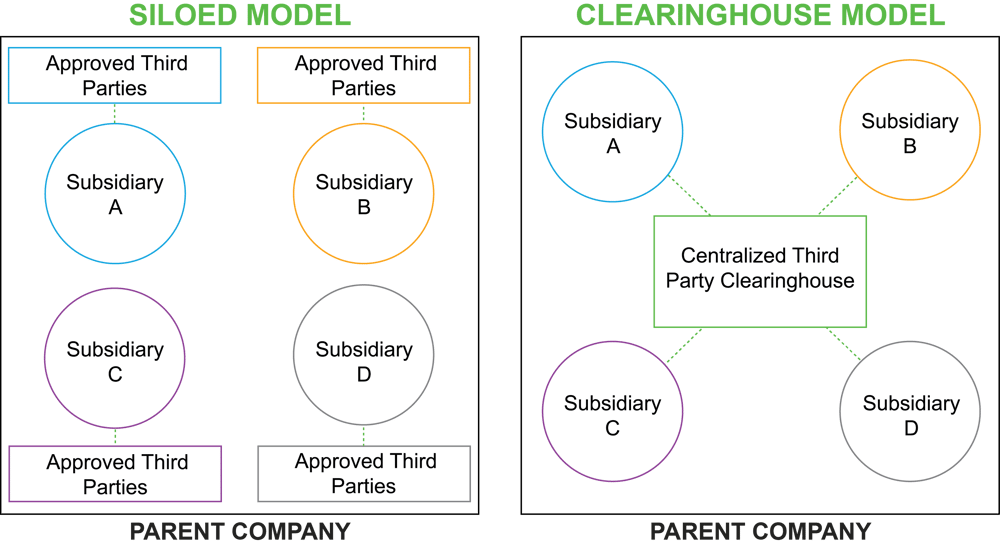
Mature TPRM programs are moving to centralized models, where costs can be controlled and better risk visibility can be provided for stakeholders across the organization.
A Broader Scope
Historically, the typical third-party risk assessment process began with Procurement, which handed off to Legal, which handed off to Information Security for due diligence. Many, if not most, organizations continue to handle third-party assessments this way. But the most mature programs are evolving this model and diversifying the types of risks that they’re assessing. Some of this has been driven by compliance concerns. The GDPR and the California Consumer Privacy Act (CCPA), for example, have forced organizations to consider the privacy risks of their vendors. To get a better view of your third-party risk, it’s important to bring more enterprise risk owners into the conversation and ensure that their specific concerns are addressed up front as part of the assessment process. By evolving your TPRM program into a more complete risk management function, you are better able to holistically profile the vendor, scoring their financial, privacy, security, operational, and reputational risk to make better decisions about their fit for your business.
More Focus on ROI
The highest-performing TPRM programs are able to demonstrate real ROI for the business, as opposed to being seen as a pure cost center. The most efficient programs have the dual function of helping the organization manage risk while also providing the organization a sense of resilience. After all, third parties can play an extremely important role in your business – reducing costs, driving efficiencies, and solving problems. By removing barriers and red tape, without increasing risk, a TPRM program can allow your business functions to safely call upon third-party expertise without fear of compromise. In addition, an efficient TPRM program will provide the ability to compare the relative risk rankings of competing third parties, allowing you to choose vendors that are less likely to have high downstream costs of risk management. This can help your business save money, despite the upfront investment in the TPRM program.
Embracing the Trends in Third-Party Risk Management
Even if your organization isn’t ready for a complete TPRM overhaul, there are many small steps you can take to begin aligning your program with that of industry leaders. Many organizations see tremendous results simply by optimizing existing technology solutions to help with the process, or by bringing in (you guessed it) a third-party firm to review existing processes.
Focal Point has a team of experts specializing in third-party risk management, including those with experience evaluating third-parties through a privacy and security lens. Whether you’re looking to enhance an existing program or build one from the ground up, Focal Point can support both your strategy and execution.
Want privacy and security updates and insights delivered straight to your inbox?
Subscribe to Focal Point's Risk Rundown below - a once-a-month newsletter with templates, webinars, interesting white papers, and news you may have missed. Thousands of your colleagues and competitors have signed up! You can unsubscribe at any time.











