Last month, The Open Web Application Security Project (OWASP) released its 2017 Top 10 for public comment, with the intention of publishing the final list this summer. OWASP is an open internet community focused on improving the security of application software, and its Top 10 is an essential toolkit for security professionals and security-conscious developers. It lists the 10 most critical web application security risks, along with detailed descriptions, example vulnerabilities and attacks, and tips on how to avoid them.
The 2017 update – the first since 2013 – is based on the analysis of vulnerabilities gathered from hundreds of organizations and over 50,000 applications and Application Programming Interfaces (APIs). Most notably, it includes new categories around insufficient attack protection and under-protected APIs. The graphic below illustrates the proposed updates from 2013 to 2017:
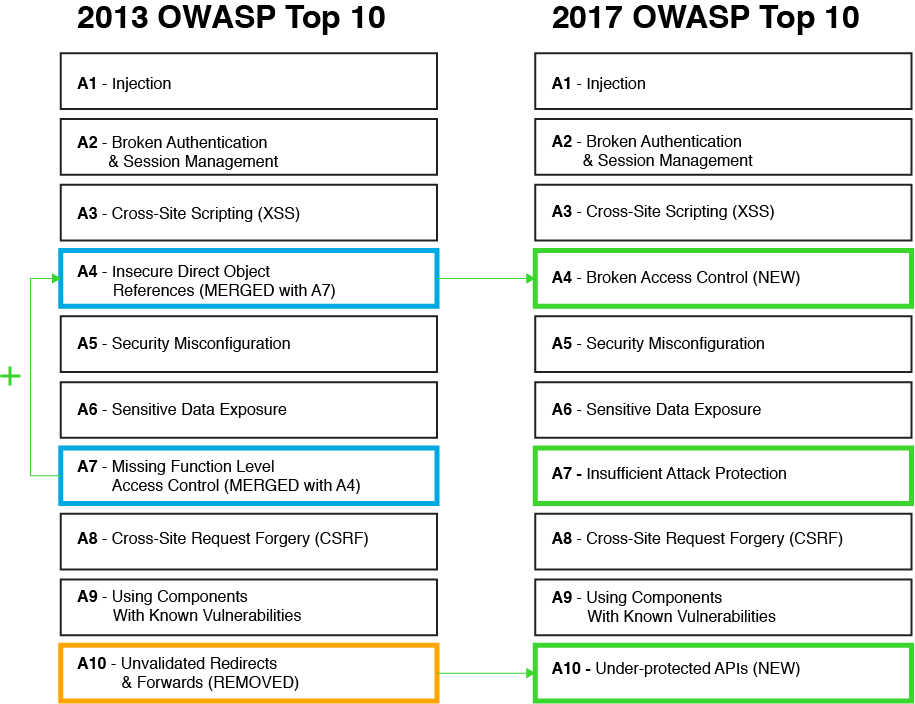
- As illustrated, 2013-A4 and 2013-A7 are now merged together as OWASP has decided that the original Broken Access Control category no longer needs to be divided into data and functionality controls.
- Also replaced is 2013-A10, Unvalidated Redirects and Forwards, which OWASP now deems as not prevalent enough to include in the list moving forward.
- Insufficient Attack Protection is now included in the list due to the number of APIs and applications lacking the fundamental ability to detect, prevent and respond to manual and automated attacks.
- Lastly, with the increasing use of APIs, Under-protected APIs has been given its own category. APIs are often left unsecured and have numerous vulnerabilities; this new category aims to bring awareness to the insufficient protection around most APIs.
The 2017 updates come at a critical time in the security world, as high-profile attacks and breaches are occurring on what seems like a daily basis. And though these updates will surely push developers to step up their game, application security is still a long way from being top of mind in the development community:
“For all the advances we’ve made at OWASP, application security isn’t part of every software project, it’s not taught regularly in university, and it’s often not viewed well by development projects. In fact, based on the OWASP T10 data we just collected, the average number of serious vulnerabilities per application is a stunning 20.5. That’s an insane number that just shows how far we have to go.” – OWASP Top 10 Co-author, Jeff Williams
The Top 10 isn’t limited to just software developers and security professionals. Its goal is to educate developers and organizations alike about the most pressing vulnerabilities and threats that applications face, and provide techniques and guidance to protect against these threats. From a risk management perspective, it can be used to gain executive sponsorship for organizations with no security program or low application security awareness. Companies need to be taking a hard look at their security practices, and the Top 10 should be the baseline for that.










