GDPR enforcement has kicked off, and the CCPA has gone into effect. With the threat of significant penalties for non-compliance looming, many organizations are placing a greater focus on data privacy. But is “checking the box” on compliance the only (or best) way to evaluate the effectiveness of your program?
Companies working to develop privacy programs that adapt with regulatory, industry, and technology change need a way to quantify and prioritize privacy risk. Privacy key risk indicators (KRIs) are designed to do exactly this. KRIs quantify the anticipated risks associated with an area of your privacy program, so you can prioritize risk mitigation appropriately, set clear objectives for your program, and establish a privacy risk appetite. In this post, we will look at how to apply KRIs, how to use the types of KRIs, and how to design a KRI framework for your privacy program.
Key Performance Indicators (KPIs) vs. Key Risk Indicators (KRIs)
Many organizations use the terms KPIs and KRIs interchangeably, but they’re actually quite different. A KPI measures the performance of individuals, business units, and projects in relation to their strategic goals and objectives. KPIs provide strategic insights into the progress of an initiative, assist in decision making, and ultimately improve organizational health. A KPI is the compass of a company, helping them stay on their strategic path.
Meanwhile, KRIs are used to determine the level of risk an organization is facing or the riskiness of a potential venture or activity. By monitoring the changes in levels of risk exposure (like loss events and assessment outcomes), KRIs can provide advanced warning to manage, mitigate, and prevent a future crisis. A KRI is a lighthouse showing you the potential risk ahead.
KRIs are important in helping executive management and board members understand the risks associated with a specific action the company is considering, as well as the inherent risks found in the company’s day-to-day operations. Executives thrive on using numerical data for decision making, and KRIs provide quantifiable metrics to indicate evolving risks and even possible opportunities. As a result, proactive decisions can be made to prevent financial, operational, or reputational issues and lead to an organization’s enterprise and risk portfolio success.
Using KRIs and KPIs
When KRIs and KPIs work together, companies are able to achieve organizational goals while effectively managing risk. By using both of these metrics, an organization can associate company goals with related risk factors to measure and monitor each simultaneously. Not only will this approach enhance an organization’s risk management strategy, certain projects and initiatives will have more success when analyzing KPIs through a risk lens.
The Different Types of KRIs
There are three types of KRIs that can be used to measure risk exposure. These KRIs look at current and past exposure as well as potential threats and the necessary mitigation actions.
Lagging Indicators
Lagging indicators monitor past events that have the possibility of taking place again. They identify changes in the pattern of risk and trends to ensure that exposure is minimized to reduce further consequences.
- A breach of personal information.
- A natural disaster impacting continuity of operations.
Current Indicators
Current indicators address your organization’s current risk exposure levels.
- The number of staff that has yet to complete a new privacy regulation training.
- The number of systems without encryption of data-at-rest.
Leading Indicators
Leading indicators are used to signal changes in the likelihood of a risk event. They are for emerging risk trends for events that might happen in the future and will then need to be addressed. They aid management in initiating action before a risk occurs.
- An increase in social engineering and phishing attacks.
- An increased amount of personal information being collected due to change in operations.
The Characteristics of Effective KRIs
For KRIs to be the most effective, they must meet a specific set of criteria: quantifiable, predictable, informative (auditable), and comparable. A good example of a KRI would be the number of incidents where customer personal data is put at risk, which can be used as an indicator for compliance, technology, and reputational risks. Let's see how this example exhibits the key characteristics of a strong KRI:
|
Key Characteristics of a KRI |
Example: The number of incidents where customer personal data is put at risk |
| Quantifiable: The indicator needs to be measurable (numbers, percentages, etc.), relatively precise, and meaningful without the need for interpretation. | Provides a precise measurement of incidents. |
| Predictable: The indicator must provide early warning signs that management can act on. | When examined over time, can demonstrate the likelihood of another incident. |
| Informative (Auditable): The indicator must measure the status of risk and control. | Illustrates how effective or ineffective the current controls are to stop these incidents. |
| Comparable: The indicator must be able to track trends over a period of time in order to put a stop to those that are negative. | Can be compared against past months’ statistics to show trends in incidents. |
Along with these attributes, management should also define the thresholds that would trigger action. Creating this preemptive approach will limit the likelihood of a risk event occurring, as well as allow management to come up with a plan to minimize the impact of these adverse events.
The risk appetite of an organization should also be considered when determining the thresholds and trigger points of a KRI. Senior management should regularly review and approve these threshold indicators to ensure they align with the companies near-term and long-term objectives.
The Challenges of Privacy Risk
Today’s privacy leaders face many challenges when managing data privacy at scale.
Many organizations are struggling to keep up with the broad range of regulatory and industry standards that are continually issued. Loaded with a complex ecosystem of data sharing models, there is no single point of ownership across an enterprise, leading to a lack of privacy responsibilities. Not to mention, over 70% of businesses are dependent on third parties, increasing the threat of a data breach exponentially. In addition, organizations have trouble determining which data is most important to them (aka their crown jewels) and the lifecycle of that data.
Managing all of these challenges is nearly impossible without a way to measure and monitor the risk. This is where privacy key risk indicators come into play. Privacy KRIs can monitor regulatory compliance, legacy storage terms, the ecosystem of data-sharing models, and more, and provide digestible pieces of information that offer invaluable insights.
What are Privacy KRIs?
Privacy KRIs are focused on solving the privacy challenges facing an organization. They measure control effectiveness across a defined privacy risk framework, which can help an organization better understand its risk appetite. Privacy KRIs measure both the cause and the consequence of a possible risk. Their main goal is to identify actionable and measurable metrics for key controls supporting an organization’s privacy program.
KRIs can often be applied to privacy notices, consent management, privacy complaints, and data retention. With proper KRIs in place, organizations can measure the cost and monitor the compliance of third parties and determine the operating efficiency of a third-party risk management program.
In order for an organization’s privacy KRI program to be effective, it must be regularly monitored. KRIs need to be tracked and reported, and tools and dashboard reporting need to be leveraged. Risk mitigation plans are an effective way to address KRI limits. Furthermore, the KRI inventory should be reassessed on a regular basis.
Examples of Privacy KRIs
| Privacy Domain | Risk | Control | KRI |
|
Third-Party Risk Management |
Unauthorized access that results when a third party exceeds or misuses access |
Third-party security due diligence is performed upon onboarding and throughout the duration of the relationship |
% of vendors with access control issues identified as “high risk” |
|
Privacy Policies and Frameworks |
The act of not following policies, standards, or procedures |
Exceptions to privacy policies are reviewed and approved through a formal risk acceptance process and revisited periodically |
# of approved exceptions to the policy not revisited within a defined period of time |
|
Privacy-by-Design |
New types of data collected on website not understood |
Privacy Impact Assessments (PIAs) are performed during the design of new features on websites, including adding/modifying data collected from customers |
% of PIAs with a moderate or above risk ranking |
The Benefits of Privacy KRIs
In response to these evolving challenges, many organizations have begun focusing on privacy KRIs in addition to compliance assessments to gain further insights into the effectiveness of their programs.
An effective privacy KRI program keeps executives better informed on the risks associated with their business, and also enables better decision making around emerging risks. Privacy KRIs aid in the achievement of specific objectives since enhanced risk monitoring and reporting identify impending risk before it’s too late. Early detection also reduces the time, effort, and expenses spent recovering from a breach or a penalty and the subsequent reputation damage.
Building a Privacy KRI Framework
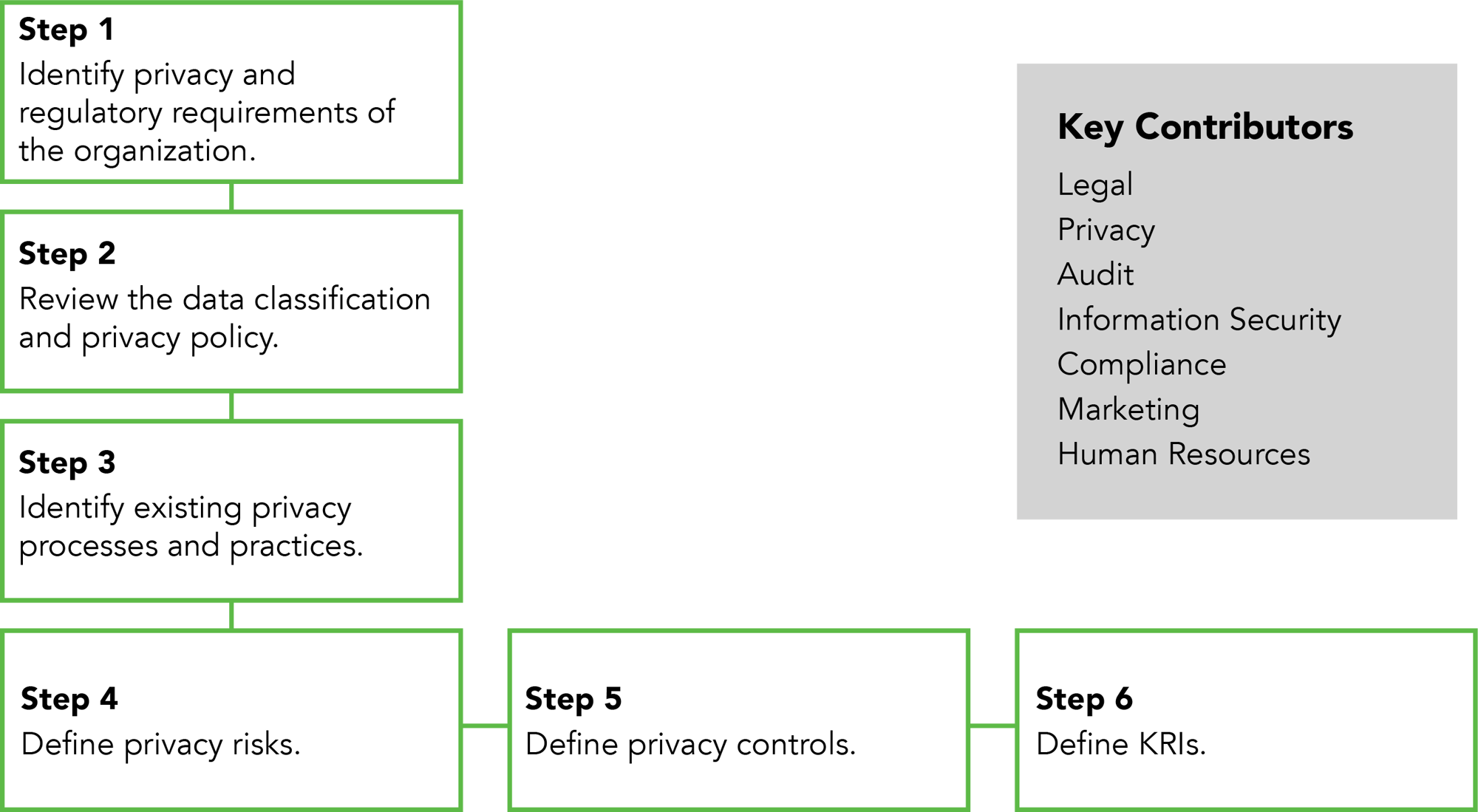
Building a privacy KRI framework requires diligent review of existing controls, policies, and compliance requirements. Using these steps as a base, you can define your privacy risks and the KRIs needed to monitor them.
- Step 1: Identify the privacy and regulatory requirements of the organization.
- Step 2: Review your data classification and privacy policies.
- Step 3: Identify existing privacy processes and practices.
- Step 4: Define privacy risks.
- Step 5: Define privacy controls.
- Step 6: Define KRIs.
Along the way, you’ll need input from various parts of the business to accurately identify the controls and policies necessary to support your KRIs framework. These typically include, but are not limited to: Legal, Privacy, Audit, Cyber Security, Compliance, Marketing, and Human Resources.
Having a comprehensive view of your privacy risks is vital to data protection. Effectively monitoring privacy KRIs will allow you to more effectively address both present and emerging risks and better understand the threats facing your organization. KRIs, in collaboration with KPIs, can ensure you are on track to meet your business objectives. While it’s hard to predict what the future holds for your organization, a solid KRI program can help.
Stay On Top of Changing Privacy Trends
Subscribe to Focal Point's Privacy Pulse below - a once-a-month newsletter with guides, webinars, interesting white papers, and news all focused on data privacy. You can unsubscribe at any time.










