Each year, roughly $600 billion is lost because of cyberattacks. In a push to protect the U.S. defense supply chain from both foreign and domestic cyber threats and security risks, the Department of Defense (DoD) created the Cybersecurity Maturity Model Certification (CMMC). This new unified standard will ensure the more than 300,000 companies in the Defense Industrial Base (DIB) supply chain have adequate practices and processes in place to protect sensitive defense information.
For the CMMC, all DoD contractors are required to be evaluated based on the maturity and reliability of their cybersecurity infrastructure, earning a certification ranging from Level 1 (basic cyber hygiene) and Level 5 (advanced security). The five CMMC certification levels are tiered, so the requirements and processes for each level builds upon the one before. Future DoD contracts will indicate the certification level required to bid, and only companies certified to the level specified or higher will be allowed to submit a proposal for those contracts.
In this five-part series, Exploring the Five Certification Levels of the CMMC, we’ll do a deep dive into each of the five certification levels to help you better understand the requirements for each and how you can achieve the certification for the level of your choosing.
Let’s take a closer look at the CMMC Level 1 Certification.
Need a quick refresher on the CMMC and its requirements?
Check out this blog for a more in-depth look at this new standard.
CMMC Level 1 Certification
Regardless of which CMMC certification level you ultimately want to achieve, you must begin by setting the controls specified in Level 1. The CMMC Level 1 certification represents the basic cyber hygiene necessary to safeguard Federal contract information (FCI), which is information not intended for public release and serves as the foundation on which the other four levels build.
Since Level 1 is focused on basic cyber hygiene, maturity processes are not assessed at Level 1. Therefore, companies do not have to create policies regulating the required practices. It is the only level to not contain any processes. Since formal documentation is not required, compliance can be shown to a CMMC auditor through any method that demonstrates the practice has been performed, including screenshots.
Although there are no processes for Level 1, there are 9 capabilities and 17 practices across 6 domains that must be met to achieve CMMC Level 1 compliance. These practices are primarily comprised of physical protection requirements and access controls. We’ll explore each domain, capability, and practice required for Level 1 compliance below.
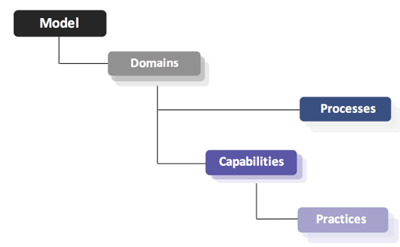 Figure 1: CMMC Model Framework (Source)
Figure 1: CMMC Model Framework (Source)
Domain #1: Access Control
This domain contains capabilities and practices to ensure companies can identify and control who has access to their internal systems.
Capability #1 – Establish system access requirements
AC.1.001
CMMC Requirement: Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems)
This practice ensures a company has access control over their network by requiring all users have unique usernames and passwords and that there is a proper provisioning and deprovisioning process in place. This practice guarantees that only authorized users have access to specific networks and systems.
Level 1 only requires that a statement be distributed to staff members specifying these mandatory practices (e.g., passwords will be required on all devices and unauthorized users, and devices will be removed from the network).
Capability #2 – Control internal system access
AC.1.002
CMMC Requirement: Limit information system access to the types of transactions and functions that authorized users are permitted to execute
Different permission levels (i.e., user vs admin) should be applied to limit who can access certain systems, software, or applications. Each staff member should have only the appropriate permissions for accessing and viewing sensitive federal information being handled during DoD projects.
AC.1.003
CMMC Requirement: Verify and control/limit connections to and use of external information systems
In 2019, more than half of the companies worldwide that used cloud services experienced a breach. For this practice, any cloud providers utilized must be reviewed, and controls to limit the access these providers have to internal networks and devices must be in place. In addition, controls should be in place to ensure only approved devices have access sensitive federal information.
Capability #3 – Limit data access to authorized users and processes
AC.1.004
CMMC Requirement: Control information posted or processed on publicly accessible information systems
Ensure that only authorized individuals have the permissions to post information on the company website or social media channels. This is to ensure classified federal information is not unintentionally made public.
Domain #2: Identification and Authentication
This purpose of this domain is to guarantee that the individual assigned to an account or device is the only one that has access to or uses it.
Capability #4 – Grant access to authenticated entities
IA.1.076
CMMC Requirement: Identify information system users, processes acting on behalf of users, or devices
Similar to the practices in the Access Control domain, unique usernames and passwords must be assigned to users accessing sensitive federal information. This also includes account names, host names, and device identifiers.
IA.1.077
CMMC Requirement: Authenticate (or verify) the identities of those users, processes, or devices, as a prerequisite to allowing access
This practice ensures that all company devices require a username and password before they can be accessed. Other forms of authentication like hardware keys, tokens, and two-factor authentication are encouraged. This includes any device that connects to the company’s network or accesses sensitive federal information, including laptops and mobile devices. All default system accounts, usernames, and passwords must also be changed or disabled.
Domain #3: Media Protection
The Media Protection domain safeguards the sensitive federal data stored on electronic devices, removable media, or even paper copies, and ensures that data is properly destroyed.
Capability #5 – Sanitize media
MP.1.118
CMMC Requirement: Sanitize or destroy information system media containing Federal Contract Information before disposal or release for reuse
All devices and paperwork that contains sensitive FCI must be cleared, purged, or destroyed. Shredders should be used for any papers, films, or CDs used. IT teams must also clear the sensitive data from any computers, mobile devices, or hard drives that accessed sensitive information. If an external vendor is used for this process, ensure a certificate of destruction is provided.
Domain #4: Physical Protection
This domain is to safeguard against a physical breach at a company’s facility by ensuring the proper controls are in place to protect the perimeter and the devices within.
Capability #6 – Limit physical access
PE.1.131
CMMC Requirement: Limit physical access to organizational information systems, equipment, and the respective operating environments
Ensure that all computers, servers, and network gear can be secured or are located in a securable area. Cameras should also be installed to monitor any physical entry to these areas.
PE.1.132
CMMC Requirement: Escort visitors and monitor visitor activity
This practice is in place to ensure proper control of the facility perimeter in order to limit access and identify anyone present in the facility. Guests should be required to sign in with their information along with their entry and exit times. Guests should also carry a temporary badge at all times identifying who they are and clearly indicating that they are visitors. Guests should be escorted at all times, as well. Employees should understand these protocols to ensure unidentified guests are reported.
PE.1.13
CMMC Requirement: Maintain audit logs of physical access
Any access to the facility for both employees and visitors must be recorded. This can be achieved through a physical log, key cards, biometric devices, or any other strategy that creates a forensic trail of the individual accessing the facility and other secured areas. This is a critical requirement for data centers.
PE.1.134
CMMC Requirement: Control and manage physical access devices
All physical access devices such as keys and badges should be inventoried and tracked. When an employee departs, the inventory can be reviewed to track which access devices they possess for proper collection. Employees should also be trained to report any missing or stolen physical access devices.
Domain #5: System and Communications Protection
The purpose of this domain is to secure a company’s system boundaries and communications.
Capability #7 – Control communications at system boundaries
SC.1.175
CMMC Requirement: Monitor, control, and protect organizational communications (i.e., information transmitted or received by organizational information systems) at the external boundaries and key internal boundaries of the information systems
A border security infrastructure (i.e., firewall) should be configured to protect the internal network. Successful implementation prevents attacks from reaching internal computers.
SC.1.176
CMMC Requirement: Implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks
Organizations that host services available to the public must implement a demilitarized zone (DMZ) – subnetworks that are physically or logically separated from internal networks. DMZs create a secure area for hosting public users without compromising the internal network. A DMZ can be implemented using techniques like routers, firewalls, gateways, or cloud-based technology. Third party vendors can also be used to host these publicly accessible systems.
Domain #6: System and Information Integrity
The capabilities and practices found in this domain are to ensure a company’s network has applied the proper protection mechanisms and has fixed security flaws in order to defend against malicious code.
Capability #8 – Identify, report, and correct information and information flaws in a timely manner
SI.1.210
CMMC Requirement: Identify, report, and correct information and information system flaws in a timely manner
This practice involves keeping all systems up-to-date with the latest security patches, system upgrades, and software and firmware updates. Automatic updates should be enabled to allow for system updates and patches as they are released. Research should also be completed to ensure devices like scanners, printers, and routers have the latest software.
Capability #9 – Identify malicious content
SI.1.211
CMMC Requirement: Provide protection from malicious code at appropriate locations within organizational information systems
This practice is for the protection against malicious code (e.g., viruses, worms, trojan horses, spyware, etc.) in designated locations (e.g., firewalls, mobile devices, emails, etc.). An antivirus program should be implemented on each device, as well. Larger organizations should scan for malicious code within emails and at the network perimeter.
SI.1.212
CMMC Requirement: Update malicious code protection mechanisms when new releases are available
All mechanisms to protect against malicious code (i.e., antivirus software, firewalls, etc.) must be checked and configured to update at regular intervals. Software reports can be reviewed to ensure updates are rolled out in a timely manner.
SI.1.213
CMMC Requirement: Perform periodic scans of the information system and real-time scans of files from external sources as files are downloaded, opened, or executed
This practice requires that any files downloaded, opened, or executed are scanned for malicious code at a regular interval. Antivirus programs should be configured to perform full scans weekly; but daily scans provide a more enhanced protection strategy.
Achieving Level 1 Certification
For many organizations, CMMC Level 1 compliance will be the easiest achieve, as they already have these basic cyber hygiene measures in place. At this level, proof of performance of these 17 practices is not required by the CMMC, just a demonstration that these controls are in place and have been communicated to your organization. While larger companies will likely use Level 1 as a foundation for a higher level of certification, smaller companies that only handle FCI (and not controlled unclassified information (CUI)) may be able to continue work with the DoD with just a Level 1 certification. All in all, with minimal costs and a bit of effort, your company can easily achieve compliance with CMMC Level 1.
Want more cybersecurity insights in your inbox?
Subscribe to Focal Point's Risk Rundown below - a once-a-month newsletter with templates, webinars, interesting white papers, and news you may have missed. Thousands of your colleagues and competitors have signed up! You can unsubscribe at any time.












