September 2019 Update: This JavaScript Security extension has been published by Burp Suite! You can install it directly within Burp, via the BApp Store feature in the Burp Extender tool.
Why compromise just one website when you can compromise a whole bunch of them all at once?
I'm sure that's what attackers were thinking in 2018 as they compromised content delivery networks (CDNs) and used them to host malicious JavaScript. And it’s a genius strategy! Compromised companies will unwittingly feed them sensitive customer data (e.g., credit card numbers), will never have any evidence of the attack, and will never know anything has changed. Meanwhile, their customers will receive malicious JavaScript libraries that the "victim" companies require them to load for a smooth customer experience. Then the sensitive information will be fed directly from the user to the attacker.
Why is this so easy? Today, more sites are relying on JavaScript to enhance the user experience, and they are doing it in a way that makes it harder to evaluate referenced JavaScript libraries: they are using JavaScript libraries to load other JavaScript libraries into the Document Object Model (DOM).
It can be challenging to track these issues down during a penetration test, especially when you have limited time and you want to deliver the highest quality results possible. To assist our partners, clients, and the security community in identifying these issues, we developed a Burp Suite extension. Burp Suite is a Java-based tool used by many security teams for web-application testing. This extension helps Burp Suite users evaluate JavaScript in use in web applications for subresource integrity and content security policy protections while comparing observed resources against threat intelligence feeds. You can download the extension for free via the BApp Store.
Preparing Your Defenses
What can you do to protect your web applications from these types of attacks? Let's talk about two defense tactics: subresource integrity and threat intelligence.
Subresource Integrity (SRI)
There is a new, simple way to prevent compromised JavaScript resources from impacting users who visit your website: subresource integrity (SRI). If you're loading an external resource, especially JavaScript, you can provide an "integrity" attribute as a part of the HTML script tag. This attribute is a SHA 256, 384, or 512 hash of the referenced resource. When the browser pulls the resource, it will check the SRI integrity attribute (where present) against the cryptographic hash of the file obtained and verify that it is the resource you intended to include, as opposed to a malicious, or altered, version of the library. The following is a properly formatted, integrity-protected tag from the JQuery CDN.
<script
src="https://code.jquery.com/jquery-3.3.1.min.js"
integrity="sha256-FgpCb/KJQlLNfOu91ta32o/NMZxltwRo8QtmkMRdAu8="
crossorigin="anonymous"></script>
SRI is supported by Chrome, Safari, Firefox, and Microsoft Edge today. You can also require that all script resources have an integrity attribute to be loaded using Content Security Policy (CSP). The following is an example of a CSP statement that requires a valid integrity attribute for all script tags.
Content-Security-Policy: require-sri-for script;
Threat Intelligence
Another great way to identify malicious JavaScript is through threat intelligence. With shared sources of information about malicious JavaScript observed on the Internet, it is possible to aggregate that intelligence and evaluate web applications for the presence of any indicators of compromise (IoCs) – for example, known malicious JavaScript paths or file hashes.
The Burp Suite Extension and its Capabilities
The Burp Suite extension we developed helps automate checks for SRI attributes, policies, and matches in threat intelligence. The extension implements a passive scan interface. When the extension is enabled and resources are being passively evaluated, they will be sent through the extension's scan engine. While it’s a passive scan, the extension does make requests for all resources and referenced resources using the Burp HTTP interface as well as Selenium via a chromedriver binary. This must be done at this time, as there is no interface to the Burp DOM evaluation engine. Selenium will obtain the page, model the DOM, and load all the JavaScript.
Requirements
You will need to obtain a chromedriver executable, which provides an interface between the Java Selenium library and a headless Google Chrome browser. You can obtain the correct files for your operating system at http://chromedriver.chromium.org/. Note the location of the chromedriver executable file for configuration.
Configuration
The extension provides a configuration tab in the Burp Suite GUI which testers can use to set the path to their chromedriver binary and adjust the wait time before Selenium considers a page to be completely loaded. The default delay is 10 seconds, but testers may vary this based on the speed of their connection, complexity of the page, etc.
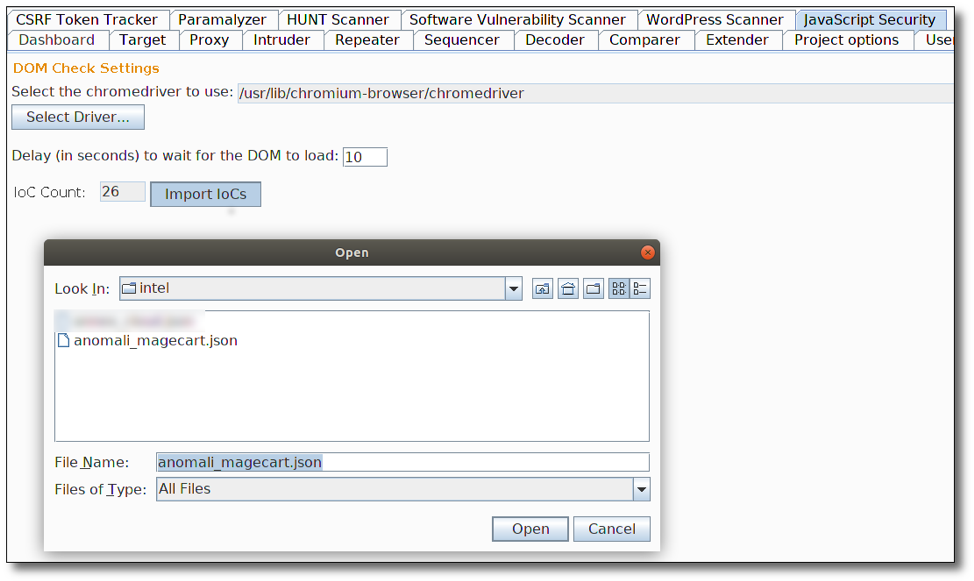
The configuration tab also gives testers a place to load threat intelligence data. IoCs pertinent to malicious JavaScript; specifically known, malicious URLs; and file hashes can be provided to the plugin as a JSON file. During evaluation, all resources will be vetted against the available intelligence.
Passive Scan Checks
Once the engine maps out each page's DOM and the referenced JavaScript resources, it will perform the following checks:
- Does each JavaScript tag use an SRI integrity attribute?
- If it does, is the SRI integrity attribute correct for the referenced resource?
- Does the CSP require SRI for all JavaScript resources?
- Are there any cross-domain scripting resources that are loaded in to the DOM and not present in the initial page?
- Do any of the referenced JavaScript resources match any available threat intelligence?
- Are any of the JavaScript resources that are cross-domain not available due to DNS issues, indicating a possibility for domain takeover?
Potential issues will be logged within the Burp Suite interface for any of these items.
Where to Get the Burp Suite Extension
The extension is available now on the BApp Store.
We hope this contribution to the community helps folks stay safe out there.
Want more cyber security insights?
Subscribe to Focal Point's Risk Rundown below - a once-a-month newsletter with templates, webinars, interesting white papers, and news you may have missed. Thousands of your colleagues and competitors have signed up! You can unsubscribe at any time.











