The Cyber Balance Sheet Report is over a month old now, and while its findings are still fresh, we’re keeping tabs on new industry reports and publications that shed light on the issues we raised, or can inspire us to look at our report from new angles. One such study is the recently released The Impact of Data Breaches On Reputation & Share Value, coming out of the Ponemon Institute, which shares myriad insights into the financial and reputational costs that companies are hit with after suffering a data breach. The full report is definitely worth the read, but what really caught our attention is their research on how data breaches affect share value, and how a strong security posture really earns its value after a breach occurs. Read the full report here.
What Makes a Strong Security Program?
“I don’t think the industry knows what a successful security program looks like to measure against it.” – Cyber Balance Sheet, CISO Perspective
One of the biggest lessons we learned from CISOs at the Cyber Balance Sheet Summit was that measuring security is extremely difficult, and there isn’t a standardized way of doing it. What we do know is that breaches are a fact of life, and not getting breached has more to do with luck than it does superior defenses. (We encourage companies to focus on minimizing the impact of breaches). In their study, the Ponemon Institute devised a security posture rating system called a Security Effectiveness Score (SES) in order to rank breached companies’ security capabilities. While the metrics aren’t perfect, they offer a basic outline of the traits that make up a strong security program, as well as the traits that make up a weak one:
High Security Effectiveness:
- Fully dedicated CISO
- Adequate budget for staffing and investment in enabling security technologies
- Strategic investment in appropriate security enabling technologies, especially enterprise-wide encryption
- Training and awareness programs designed to reduce employee negligence
- Regular audits and assessments of security vulnerabilities
- A comprehensive program with policies and assessment to manage third-party risk
- Participation in threat sharing programs
Low Security Effectiveness
- Lack of incident response plans
- Inadequate funding for staffing and investment in enabling security technologies
- Frequent turnover of IT security personnel
- Poor data retention practices
- The C-suite values productivity of workforce over security
- Lack of collaboration between lines of business and IT security in determining IT security priorities
How Security Affects Share Value After a Breach
Using the SES metric, the study found that, of companies that experienced a data breach, the stock values of those that scored a higher SES value recovered more quickly than the companies that had a lower SES value.
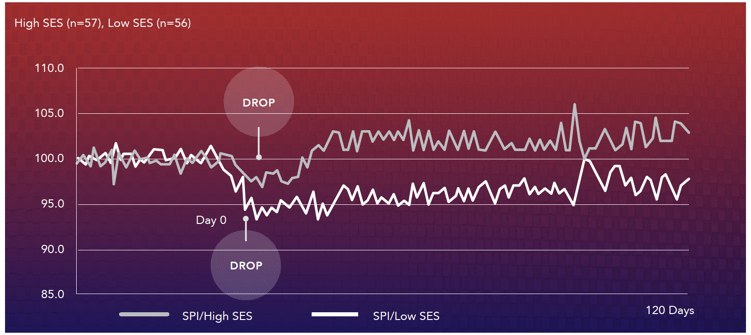
| Comparison of high vs. low Security Effectiveness Score (SES) subsamples over 120 days - The Impact of Data Breaches on Reputation and Share Value, Ponemon Institute and Centrify |
For companies that had a high SES, stock value dropped no more than 3% after the breach, and made a full 3% recovery after a 90 day period. The highest scoring companies were able to fully recover their stock value after only 7 days following the breach. Contrast that with the low scoring companies who experienced a significant decline following the breach, and were not able to recover from it after more than 90 days. This analysis was based on 113 publicly traded companies who notified breach victims and regulators about the breach, and completed the SES survey shortly after containing it.
The study echoes what we’ve been saying about the inevitability of breaches. The most well-prepared companies are the most well-protected, and having the right practices with the right people in place will allow you to mitigate the financial and reputational impact that breaches pose.










