Twitter, Facebook, Instagram, and LinkedIn are ever-present in our lives, and mostly used for innocuous purposes – funny memes, pictures of our kids and grandkids, and following celebrities.
But these seemingly innocent platforms can also bring down your business.
Let’s look at a few key threats on the rise on social media, and then we’ll leave you with a social media security policy template you can use at your organization.
Threat 1: Phishing Attacks
Social media phishing attacks increased by 500% in 2016. The personal nature of social media makes it easy for hackers to gather intel on targets, so this type of attack is often successful. ZeroFox found that 66% of spearphishing attempts spread through social media were successful, while email phishing has a 30% success rate.
This success has introduced a new type of phishing into our world: angler phishing. During an angler phishing attack, a hacker creates an imitation customer support account on Twitter or Facebook and then monitors a brand’s actual customer support account for tweets from customers looking for assistance. It then immediately reaches out to the customer and provides them with a link to “get help.” Then they reel the customer in, asking for personal info like their online banking logins, social credentials, personally identifiable information (PII), and credit card info.
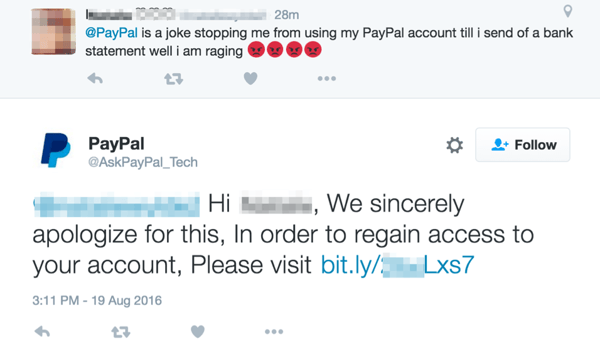 |
| A real customer requests support, and a fake PayPal account (@AskPayPal_Tech) responds. |
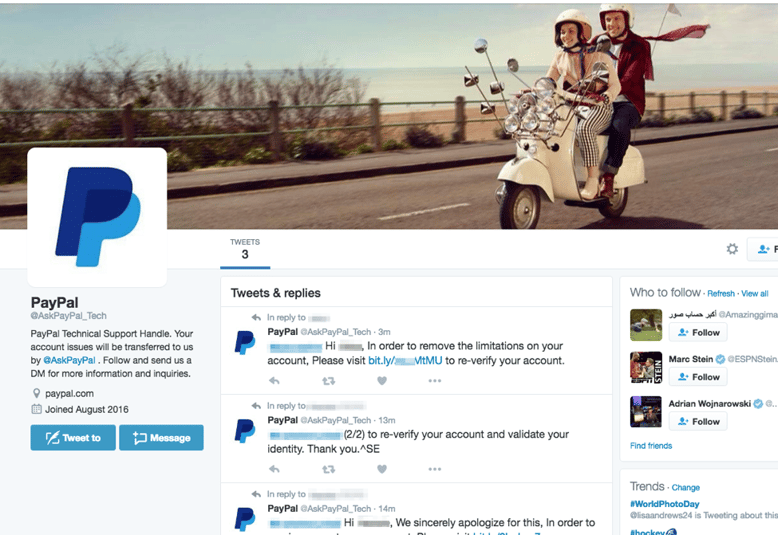 |
| The fake PayPal Twitter account, complete with stolen branding. This account has since been shut down. |
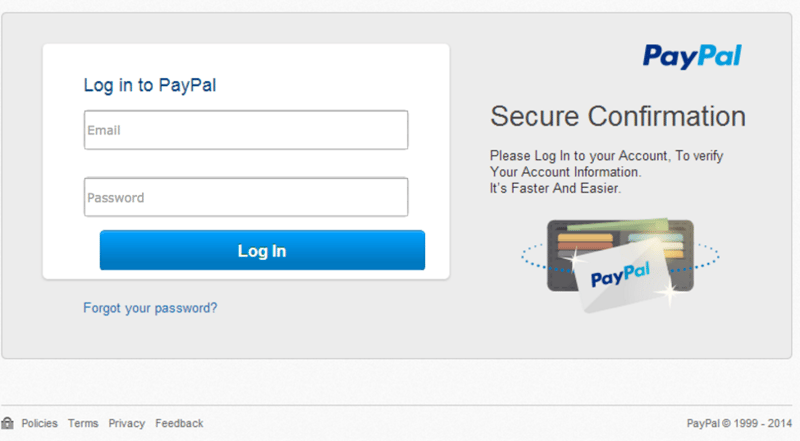 |
| A fake login screen with unlicensed PayPal branding. Thanks to ProofPoint for capturing the screenshots. |
These types of phishing attacks have two victims: customers and brands. Customers lose control of critical data and many times even experience financial loss. But on top of that, this type of attack can ruin a brand’s relationship with their customers and lead to negative publicity.
Threat 2: Malware Attacks
Social media may seem like an unconventional channel to spread malware, but malware developers are anything but conventional. In the past few years, we have seen malware evolve in increasingly viral and destructive ways. Malware creators have even developed methods to attach malicious code to photos and other highly shareable social content.
The most notorious example of this is the 2016 Locky ransomware attack. The attackers behind Locky (later dubbed “Image Gate”) exploited vulnerabilities in Facebook and LinkedIn that downloaded images laced with malicious code onto users’ devices. If users opened this download, they were met with a ransom note and their files were locked.
Because images are one of the most shared types of content on social media, image-embedded malware can spread like wildfire across social platforms.
URL shortners – ubiquitous on every major social media platform – can also be used to conceal malware sites, hiding suspicious-looking domains behind short, randomly-generated URLs.
Threat 3: Your Employees
Possibly the greatest threat to a company on social media is its employees, for two main reasons: human error and oversharing. Whether it’s company representatives leaking confidential information on Twitter or your social media coordinator making an honest mistake, this type of oversharing can cause the most damage to your brand.
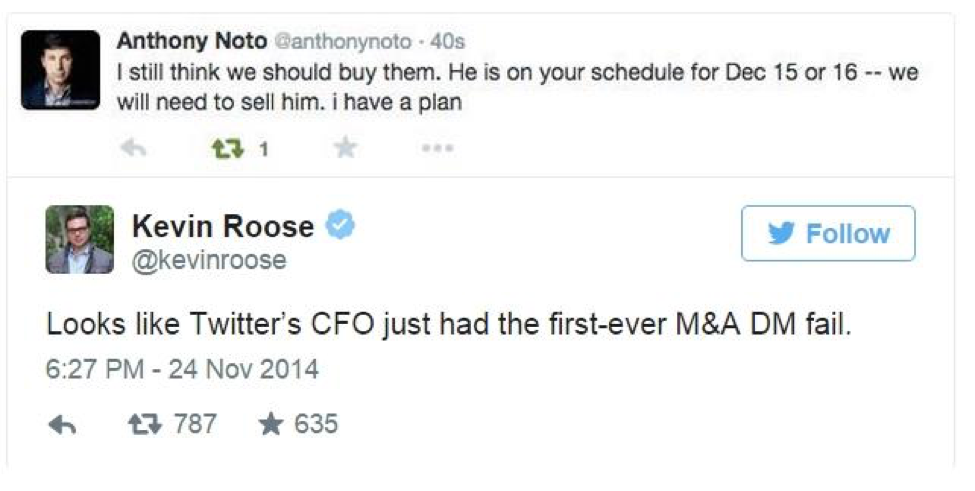
It happens to the best of us. Twitter’s CFO confused his DMs (direct messages) with his tweets and sent an M&A message out into the Twittersphere.
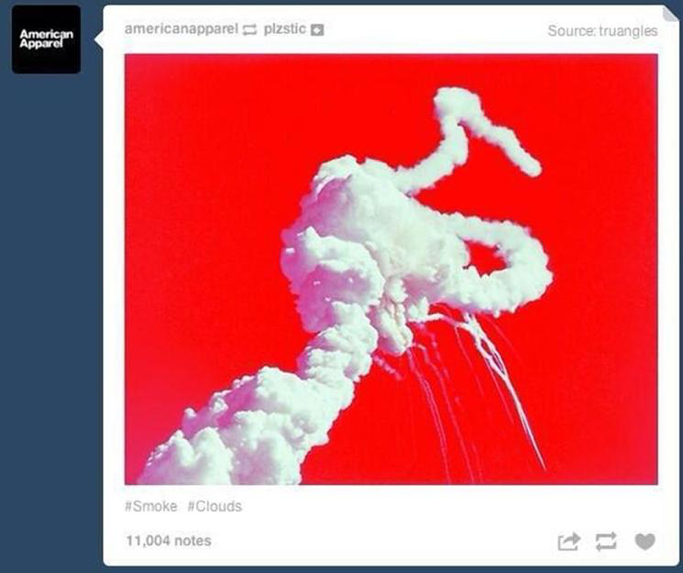
American Apparel attempted to share an artsy photo of fireworks on Independence Day 2014, but instead posted a photo of the 1986 Challenger explosion on their corporate Tumblr, which was immediately met with serious backlash.
What makes these threats so formidable is that there is no simple solution to fighting them. Awareness and security training can enable your social media management team to recognize and mitigate threats and all employees should be made aware of rising threat trends. A solid social media management tool can also help you monitor threats and control what is posted from your corporate accounts. But neither of these options can guarantee protection. But a strong social media security policy that holds your employees accountable to security best practices, documents security controls specific to social, and includes a clear response plan can make a difference.
Social media is a powerful tool for your business. To help you find the balance between being social and being secure, we’ve done some of the heavy lifting for you. In the following section, you’ll find a draft social media security policy. It should be tailored to your company’s structure, security needs, threat landscape, and unique voice. We hope you find it helpful, and if you have any questions, don’t hesitate to reach out.
A quick disclaimer: This corporate social media security policy is only focused on securing your social media channels. This is not meant to replace your social media policy, which should include items like brand representation guidelines, content requirements, and roles and responsibilities.
Template: Corporate Social Media Security Policy
Overview
[Company Name] recognizes that social media has become an integral part of our business and a key tool in our marketing strategy. It has expanded our ability to interact with our customers at a personal level, provides us with a platform to spread brand awareness, and gives our company a unique voice in the world of [insert industry type]. For these reasons, we want to continue the use of our corporate social media accounts; however, the social media threat landscape is expanding rapidly. To protect our reputation, customers, and employees from these threats, we are implementing this corporate social media security policy, which will hold us accountable to cyber security best practices as they pertain to the realm of social media.
Members of both the social media and cyber security teams are required to review this policy on an annual basis and make updates as needed. In the event of a security incident, this policy should be reviewed as soon as possible to identify any opportunities for improvement.
[Company Name] Social Presence
This policy applies specifically to the security of [Company name]’s corporate social media channels. Employees seeking guidance on personal social media usage should review our social media policy [[link to policy]].
Sections of this policy apply to the social media channels listed below:
Corporate Accounts
[[List platforms and handles here]]
Main Contact:
Brand Representative Accounts
[[List platforms, handles, contact info here]]
Access Management
Access to [Company Name]’s corporate social media accounts and credentials must be limited to those that need access to perform their job responsibilities. Those with access to corporate accounts speak as the organization on social media and interact directly with customers and must be held accountable for this responsibility.
To manage access to [Company Name]’s corporate social accounts, [Company Name] has implemented [social media management tool such as Buffer, HubSpot, Hootsuite, etc.]. Outside of this tool, only the [social media manager/coordinator/head of marketing] and the CISO have access to the login credentials for the company’s [names of select platforms] accounts. Select others within the Marketing team (or those approved by Marketing) have access to post or review content through [social media management system].
Password Management
The [social media manager/coordinator/head of marketing (referred to as social media manager from here on)] is responsible for creating passwords that meet our corporate password standards for all social media platforms. The social media manager is also expected to update credentials for all social media accounts regularly (every 90 days). If credentials for one of these social platforms are compromised, the social media manager must take immediate action to change the current password on that platform. New credentials must be provided to the [CISO, director of cyber security, etc. (referred to as CISO from here on)] upon creation.
The CISO also has the credentials for all social media accounts in order to manage access and review, monitor, and/or respond to malicious interactions or attacks via social media. In addition, the CISO is responsible for ensuring social media credentials meet the corporate password policy. As part of this, the CISO must enforce quarterly updates to all credentials.
[Social Media Management Tool]
The social media manager is responsible for designating access to [Social Media Management Tool]. Access levels are assigned based on job responsibilities.
The social media manager has the ability to grant temporary access to certain employees. He/she has provided the CISO with the list of employees who have been granted access to the tool and will provide an updated list whenever a new employee is given access. The CISO has the right to deny or remove access to employees on the list.
Employees with access to the tool must create their own login credentials for the tool. These credentials are governed by the policies set forth in the corporate password policy.
The social media manager must use [Social Media Management Tool] to manage all social media accounts. Posts should be created and scheduled on this platform and interactions and metrics are monitored within the tool. However, if the social media manager is unable to access the social media tool at a certain time (e.g., traveling, at an event, etc.) or the tool doesn’t support a certain file type (e.g., gifs), it is permissible for them to share directly from the social platform.
Mobile Device Access
Because of the “in the moment” nature of social media, [Company Name] recognizes that those managing and posting to our corporate social media accounts need the capability to post from mobile devices at events, on the road, etc. These employees are permitted to have the [Social Media Management Tool] app on their mobile devices. The social media manager is expected to also have the [insert social platforms (Twitter, Facebook, etc.)] app(s), so he/she can monitor notifications and make updates to privacy settings or passwords in the event of an emergency.
Those with access to social accounts on their mobile devices must secure those devices by following our corporate mobile device management policy, which can be found [[insert location]].
Social Media Privacy Provision
All communications posted from our corporate social media channels or by our brand representatives must follow the provisions made in our corporate privacy policy, which can be found [[insert location]]. All posts from our corporate platforms must be reviewed and approved by the social media manager, who is responsible for determining if the content could violate any part of the corporate privacy policy. If the social media manager is unsure, he or she should contact [insert appropriate party such as legal].
Social Media Security Monitoring
Monitoring is a critical part of social media security. Because social media is our most public communication platform, we may be met with comments, direct messages (DMs), mentions, and fake accounts from customers, prospects, candidates, and malicious attackers. We must monitor these interactions to identify suspicious behaviors that could result in a malicious attack.
The social media manager must set up a monitoring feed within [Social media management platform] for the handles of each corporate account, brand representative, and executive. In addition, feeds must be set up for company hashtags and similar names, so the company can monitor for fraudulent accounts.
The social media manager is required to review the feeds for corporate handles [insert appropriate interval here] and for brand representatives [insert appropriate interval here]. If he/she notes any usual activity or interactions, he/she should immediately send a report with screenshots to the CISO. The CISO is required to review any reports from the social media manager immediately. In addition, the CISO, or a member of his team, is required to review corporate account feeds on a [insert appropriate interval here] basis.
Examples of suspicious or unusual behavior include:- Spam messages or posts
- Aggressive or inappropriate DMs or mentions
- Comments or messages with suspicious links
- Repeated messages from an unknown source
- Fraudulent accounts that imitate company branding or naming conventions
- Fake accounts that imitate the names of brand representatives and mimic their behaviors
- Unusual or unexpected log-in notifications
All reports of suspicious behavior should be logged by the cyber security team and reviewed on a [insert appropriate interval here] basis by the CISO. Any patterns or trends should be noted and communicated to the social media team so they can monitor for future instances. The CISO should meet with the social media manager monthly to discuss these trends, any security concerns, any updates, and a strategy to address them. In addition, brand representatives should alert the social media manager and CISO of any suspicious or unusual interactions with their accounts.
Social Media Audits
To regularly evaluate our social media practices and improve our social media security, [Company name] requires its social media and cyber security teams to perform regular audits of its social media channels. These include:- Privacy setting audits
- Password audits
- Access control audits
- Account audits
Based on the findings of these audits, the social media manager and CISO may make updates to this policy and social media procedures to improve the security of our corporate channels.
Privacy Audits
The social media privacy audit requires the social media manager to review the privacy settings for each social platform and make updates based on any platform-wide changes to privacy settings, recent security incident, or recent cyberattacks trends. The social media manager should send the CISO a report of any changes he/she makes to the privacy settings during this audit. The CISO should review and approve/reject any changes immediately. Privacy audits should be performed semi-annually, and when a platform rolls out a significant privacy update.
Password Audits
The social media password audit requires the social media manager to update credentials for all social accounts on a quarterly basis. New passwords should meet the standards of the corporate password policy and should be reviewed and approved by the CISO. The social media manager should keep a password change log. In the event of a cyberattack or a compromise of a social platform, the social media manager should update the relevant passwords immediately.
Access Audit
The social media access audit requires the social media manager to evaluate the list of those with access to [social media management tool] on a [insert appropriate interval here] basis. Upon termination of an employee who had access, the social media manager should revoke their access to the tool immediately. If an employee had temporary access, this access should be revoked at the end of the specified time period by the social media manager. This audit is to ensure that no revocation of access has been overlooked.
Account Audit
The social media account audit requires the social media manager to assess the current list of social accounts and perform a search on similar names and handles to identify any fraudulent accounts. Any account that is deemed fraudulent should be brought to the attention of the CISO. The social media manager should report this fraudulent account to the social platform to ensure it is taken down.
Testing
With the rise of phishing scams on social media, it is critical that the CISO test social media cyber security procedures. A key component of this is testing the social media team and brand representatives to protect against phishing scams. On a [insert appropriate interval here] basis, the cyber security team should issue social media phishing scenarios to test the social media team. These tests must be approved by the CISO, and [head of marketing] must be alerted.
These tests should mimic trending social media phishing attack methods to keep the social media team aware of current threats. Based on the results of the tests, cyber security and social media teams should work together to enhance security practices where possible and to improve overall security.
Social Media Incident Response Planning
In the unfortunate event that a cyber security incident occurs via social media, the social media manager and CISO shall execute the following workflow.
[Social media incident response plans may be included in your corpoarate security incident response plans, instead of your social media security policy. Due to the unique structure of each organization, variations in points of contact, mitigation tactics, review processes, and follow-up procedures will vary. However, we’ve provided a very loose structure below for common attack scenarios.]
Phishing Attack: Malicious link clicked and corporate credentials or proprietary information compromised.
- Alert the CISO immediately.
- Change passwords to all social accounts, as well as any other compromised accounts.
- CISO and cyber security team examine the attack and the impact on the organization.
- CISO and cyber security team develop and execute a strategy for mitigation.
- CISO and cyber security team identify any opportunities for improvements around social media security procedures.
- CISO and cyber security team provide awareness training specific to this attack scenario to the social media team.
Malware Attack: Malware downloaded onto device(s). Poses enterprise-wide threat.
- Alert the CISO immediately.
- Change passwords to all social accounts.
- CISO and cyber security team examine the malware and the extent of the attack across the organization.
- CISO and cyber security team develop and execute a strategy for mitigation.
- CISO and cyber security team identify any opportunities for improvements around social media security procedures.
- CISO and cyber security team provide awareness training specific to this attack scenario to the social media team.
Social Media Credentials Compromise: Attacker gained access to corporate accounts or a brand representative’s account. Posting on behalf of organization.
- Alert the CISO immediately.
- Change passwords to all social accounts.
- Report to social platform.
- CISO and cyber security team examine the attack and the impact on the organization.
- Social media team drafts and shares post addressing attack with all followers.
- CISO and cyber security team identify any opportunities for improvements around social media security procedures.
- CISO and cyber security team provide awareness training specific to this attack scenario to the social media team.
Brand Reputation Threat: An inappropriate or “off-brand” post is shared on a corporate account or a brand representative’s account.
- Delete the post immediately.
- Alert the social media manager immediately.
- Monitor notifications for any negative response from followers.
- Coordinate with marketing and/or public relations team on response.
- Assess the current review process for all corporate posts, and evaluate the access level of the employee who shared the post. Review content guidelines with social media team and brand representatives.
- If warranted, take disciplinary action.
Response plans and workflows must be tested on an annual basis by the social media and cyber security teams.
Training
Training is a key component of every social media security program. It ensures all parties involved are aware of recent threat trends, understand their roles in protecting against threats, know how to react appropriately in the event of an incident, and can implement smart strategies to protect against future cyberattacks from social media.
Every member of the social media management team is required to complete social media security awareness training upon hire and then on an annual basis. This training includes sections on:
- Common threat trends and methods
- Overview of recent attacks (including industry-specific examples)
- History of attacks within the organization
- Social media security policies and procedures
- Passwords and access management
- Privacy settings
- Monitoring
- Audits
- Testing
- How to recognize a social media phishing attempt
- How to identify and avoid a malware attack
- Social media team roles in the event of an attack
This training is led by members of the cyber security team. It is reviewed and updated on an annual basis (unless an incident occurs, in which case it is updated immediately after) to include trends and news from that year, as well as any changes in policies or procedures.
In addition to providing social media awareness training to the social media and marketing teams, portions of this training may be extended to other relevant departments within the organization as well as brand representatives.
Want more awesome templates like this?
Subscribe to Focal Point's Risk Rundown below - a once-a-month newsletter with templates, webinars, interesting white papers, and news you may have missed. Thousands of your colleagues and competitors have signed up! You can unsubscribe at any time.










