A recent Cisco study found that 80% of consumers are willing to act to protect their privacy, saying they would spend more time and money to do so and that they consider it a buying factor. Nearly half of these respondents also indicated that they had switched companies over data privacy policies or data sharing practices. Privacy is no longer just about regulatory compliance – it has become a critical part of doing business and a competitive differentiator for many organizations.
More organizations are seeking to implement privacy policies and programs that protect consumer data and give consumers control over their data, while still meeting business needs. But this is not any easy goal to accomplish. New technology, shifting business needs, and multiple, sometimes disparate, privacy regulations like the GDPR and the CCPA all add layers of complexity to this challenge.
To help organizations address this, NIST announced its plan to develop a privacy framework based on the structure of its Cybersecurity Framework (CSF) in 2018. After a year of collaborating with businesses, government agencies, academics, industry experts, and non-profits, the preliminary draft was released for feedback in 2019. Finally, in January 2020, Version 1.0 of the NIST Privacy Framework: A Tool for Improving Privacy though Enterprise Risk Management was published.
Purpose of the NIST Privacy Framework
The NIST Privacy Framework aims to provide a set of privacy protection strategies that organizations can employ to improve their approach to using and protecting personal consumer information. It is designed to be a voluntary tool that helps organizations:
- Build consumer trust
- Manage privacy risks
- Clarify privacy management concepts
- Identify privacy outcomes and achieve privacy goals
- Demonstrate compliance with current privacy regulatory obligations
- Facilitate communication about privacy practices with consumers, employees, executives, and stakeholders
The Privacy Framework is not prescriptive, allowing for a wide application of approaches. Organizations can use its risk and outcome-based standards to mitigate privacy risks in the development of products and services, service delivery, and supply chain management, or use it when conducting the privacy impact assessments that specific regulations require. Rather than a simple checklist of tasks to perform, the Privacy Framework contains the building blocks for privacy protection, helping organizations prioritize privacy risks and outcomes and achieve privacy goals, regardless of business size, sector, or industry.
Recognizing the changing nature of technology, business operations, and the regulatory landscape, NIST considers the Privacy Framework to be a “living document,” and will continue to update it over time to contribute to the improvement of privacy.
The NIST Privacy Framework and the Cybersecurity Framework (CSF)
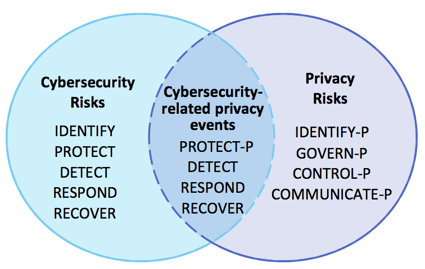
While cybersecurity and privacy should be deeply intertwined, they are not the same function, and different measures are required to properly address each area. Organizations that have adopted the NIST CSF may have a strong security program in place, but this does not mean they have adequately addressed privacy risk. Realizing this gap, NIST created the Privacy Framework. This framework uses the same structure as the CSF, making it easy for companies to align the two. When working in tandem, the Privacy Framework and CSF enhance consumer privacy, streamline compliance, and create a holistic enterprise risk management tool for organizations.
 |
| Image Source: NIST Privacy Framework |
The NIST Privacy Framework Structure
Built on the foundation of the Cybersecurity Framework, the Privacy Framework is also composed of three main parts: The Core and its Functions, the Profiles, and the Implementation Tiers.
The Core
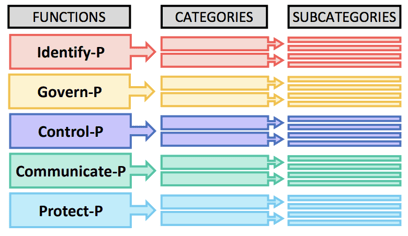
The Core is a set of activities and outcomes designed to enable internal communications about privacy protection within an organization. The Core is divided into five Functions, which are used to organize foundational privacy activities in a way that addresses the dynamic nature of privacy risk. The five Privacy Framework Functions include:
- Identify-P: Develop an understanding of the business environment to effectively identify and prioritize privacy risks
- Govern-P: Define the rules to address privacy risks and the privacy policies to meet risk and regulatory requirements
- Control-P: Manage data in-line with the appropriate governance structure
- Communicate-P: Establish reliable lines of communication to convey privacy risks and controls
- Protect-P: Develop and implement the appropriate data protection safeguards to prevent cybersecurity-related privacy events
The first four Functions are targeted at the privacy risks that originate from data processing. The last Function addresses the privacy risks that can lead to cybersecurity incidents. Protect-P can be augmented with the CSF Functions to collectively address privacy and cybersecurity risks. Organizations are not limited to connecting just the Protect-P function, though. The Functions from both frameworks can be used in varying combinations to manage many aspects of privacy and cybersecurity risk.
In addition, the five Functions have associated Categories (privacy outcomes closely tied to programmatic needs and particular activities) and Subcategories (specific outcomes that help support the achievement of the outcomes in each Category). These Categories and Subcategories go into greater detail on each Function, guiding organizations as they map out the data processing activities within their systems. The outcomes revealed in the Core provide the insights necessary for the Profiles section of the framework.
 |
| Image Source: NIST Privacy Framework |
Some examples of the goals, activities, and outcomes associated with the Functions can be found in the table below.
| Goals | Activities |
Outcomes |
|
| Identify-P |
Gain a clear view of how data is processed within the business environment |
|
|
| Govern-P |
Establish a defined system of policies and processes that manage privacy risk and meet compliance requirements |
|
|
| Control-P |
Implement policies and procedures that effectively manage personal information |
|
|
| Communicate-P |
Communicate privacy policies and procedures to the business |
|
|
| Protect-P |
Establish strong security controls that protect personal information |
|
|
The Profiles
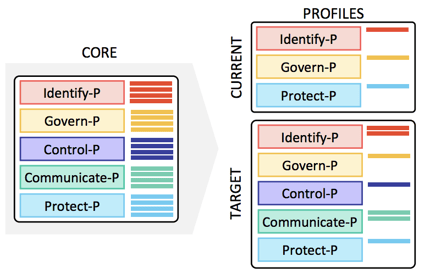
The Profiles represent the specific Functions, Categories, and Subcategories that have been prioritized by an organization based on its privacy values, business goals, and risk landscape. After analyzing outcomes and activities in the Core, organizations can develop a Current Profile and Target Profile to improve privacy practices and monitor progress.
A Current Profile (the “as is” state) documents an organization’s current privacy outcomes, while a Target Profile (the “to be” state) lists the outcomes needed to achieve the desired privacy risk management goals. The two Profiles assist the organization in identifying gaps, developing an action plan for improvement, determining the resources necessary to achieve privacy goals (e.g. staffing, funding, etc.), and improving the communication of privacy risk across the enterprise.
Depending on the organization, not every outcome or activity addressed in the Core needs to be achieved. For that reason, the Profile templates can be modified and adapted to the needs of the business. An organization can choose to tailor the Functions, Categories, and Subcategories, or develop additional ones to account for any unique risks. An organization should determine its specific needs by considering the following:
- Business objectives
- Privacy values
- Risk tolerance
- Legal/regulatory requirements
- Industry best practices
- Risk management resources
There is also no specified order of development for the Profiles. For instance, a Target Profile can be created first to focus on the desired outcomes for privacy and then a Current Profile can be developed to discover any potential gaps. Additional Profiles can also be created for different organizational components, systems, products, or services.
 |
| Image Source: NIST Privacy Framework |
The Implementation Tiers
The Implementation Tiers are designed to facilitate a more agile approach to risk management by enhancing the decision-making process and optimizing the resources dedicated to managing privacy requirements and risks. Selection of each Tier should be based on the organization’s Target Profile. The four distinct Tiers include:
- Tier 1: Partial
- Tier 2: Risk Informed
- Tier 3: Repeatable
- Tier 4: Adaptive
These four Tiers help organizations evaluate four components of their privacy program: privacy risk management practices, the level of integration of privacy risks into the enterprise risk management portfolio, data processing ecosystem relationships, and workforce structure and training programs. An organization can also use the Tiers to communicate internally about resource allocations and provide a benchmark for how an organization views and manages privacy risks.
While the Tiers represent a progression, not all organizations need to move in a linear pattern or through all the Tiers. When the processes or resources at a Tier are no longer able to effectively manage privacy risk, progression to a different Tier is warranted. Successful implementation of the Privacy Framework is based on whether the outcomes described in the Target Profiles are achieved, rather than which Tier an organization is able to progress to.
Privacy is a critical part of business operations today, but many organizations are struggling with building a strong privacy program. Without a clear framework, companies have been left to build ad-hoc privacy programs, jumping on new regulatory requirements as they arise. This has left privacy teams with duplicate, disparate privacy efforts, frustrated employees and customers, and fears of fines and penalties.
With the release of the Privacy Framework, NIST strives to provide an effective, scalable way for organizations to address privacy challenges and achieve privacy goals, which includes compliance with privacy regulations around the world. By adopting this framework, organizations will have streamlined, sustainable processes for keeping up technological advances and business changes, managing privacy risks, and enhancing consumer privacy.
Focal Point's Privacy Maturity Assessment is built on the NIST Privacy Framework, Generally Accepted Privacy Principles (GAPP), and HIPAA Breach Notification requirements and designed to help companies streamline and strengthen their privacy programs.
Get more insights into the latest privacy news.
Subscribe to Focal Point's Privacy Pulse below - a once-a-month newsletter with guides, webinars, interesting white papers, and news all focused on data privacy. Thousands of your colleagues and competitors have signed up! You can unsubscribe at any time.











